As a developer, you may have faced some scenarios that your company have multiple AWS accounts and you need to access both from difference AWS IAM accounts. If you want to perform some task for a little period of the time in another AWS account that your company own, what is best practice to do it?
Maybe you can think that Admin can create 2 accounts from those accounts and share the user credentials with you. Yes, it will work but best practice is using IAM Roles in this kind of scenarios.
An IAM role is an IAM identity that you can create in your account that has specific permissions. An IAM role is similar to an IAM user, in that it is an AWS identity with permission policies that determine what the identity can and cannot do in AWS. However, instead of being uniquely associated with one person, a role is intended to be assumable by anyone who needs it. Also, a role does not have standard long-term credentials such as a password or access keys associated with it. Instead, when you assume a role, it provides you with temporary security credentials for your role session.
This is the official introduction in Role in AWS User Guide.
Simply, Role will assume that you have the relevant permission to perform a task in a different AWS account within this context. There are few other things you can do with a Role and for those please refer the above guide.
Okay, in this example let’s assume that I am using Development AWS account and try to perform a task
First, get the Account ID from the developer account (You need to log in with a user that have admin rights). Once you log into IAM panel, left side bottom corner you will see the Account Id.
Now you need to create a Role in the Production account. Before that Role, we need to create permission Policy. This policy will define what can do to the user that login from the Developer account.
Go to production account and first create this policy in there. This the policy that we are going to use.
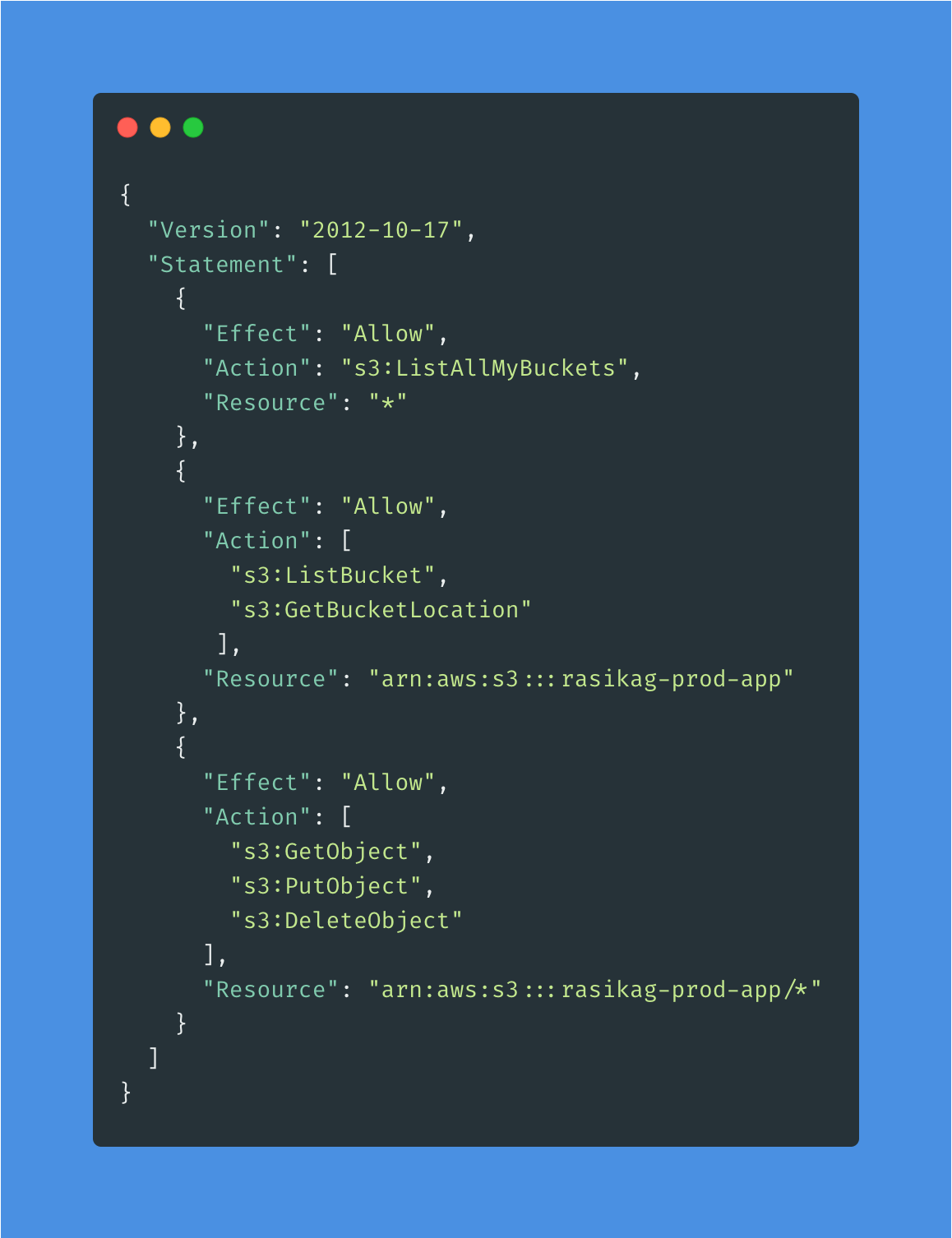
Give a name to your policy. I will name it read-write-prod-app-from-dev. Below you can see the policy creat screen.
Now we are going to create the Role. Click on Role and Create role from IAM Dashboard. Select the Another AWS account option.
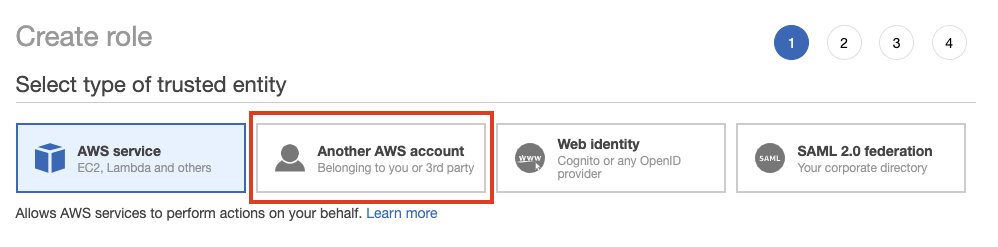
After selecting it, place dev account Id in there and remain the Required external Id and Required MFA unchecked.
Then the next window selects the permission policy. We already created this policy. Search the “read-write-prod-app-from-dev” and select it.
In the permission boundary section, I left with Create role without a permission boundary option.
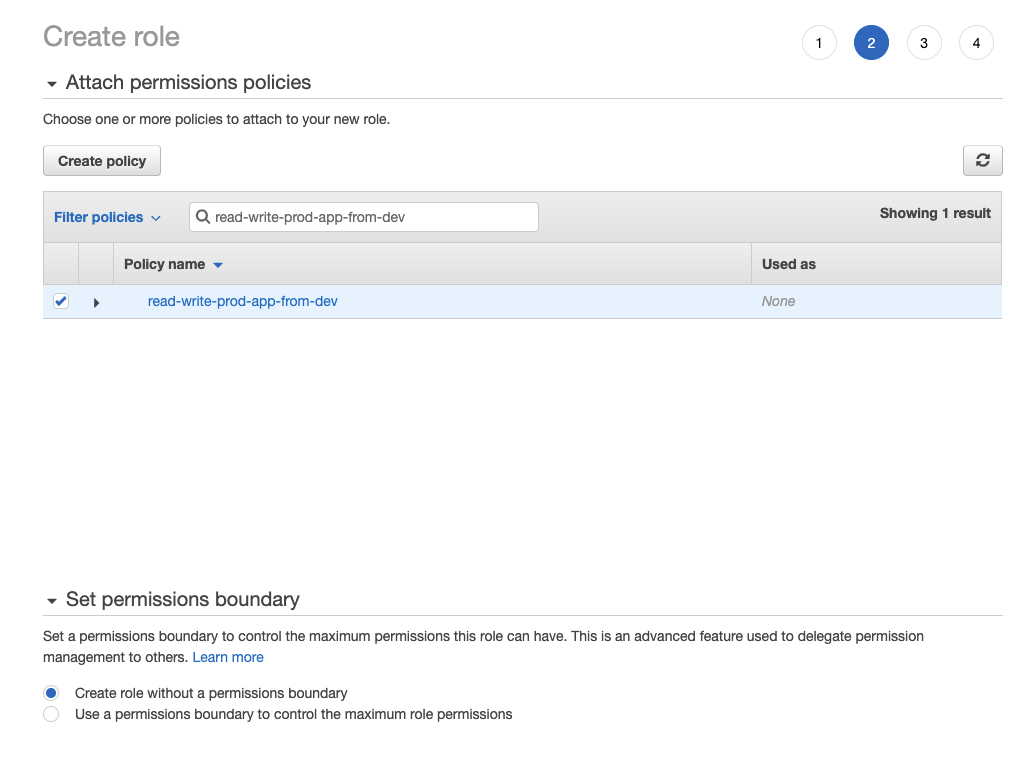
I left the tags along for this example.
Next, create the role named “UpdateProdApp”. Then create the Role.
Okay once we have done this, we create the trust between Development AWS account and a Production AWS account. From the roles panel, select the UpdateProdApp role and copy the ARN value. Because we need that value to use in Development AWS account.
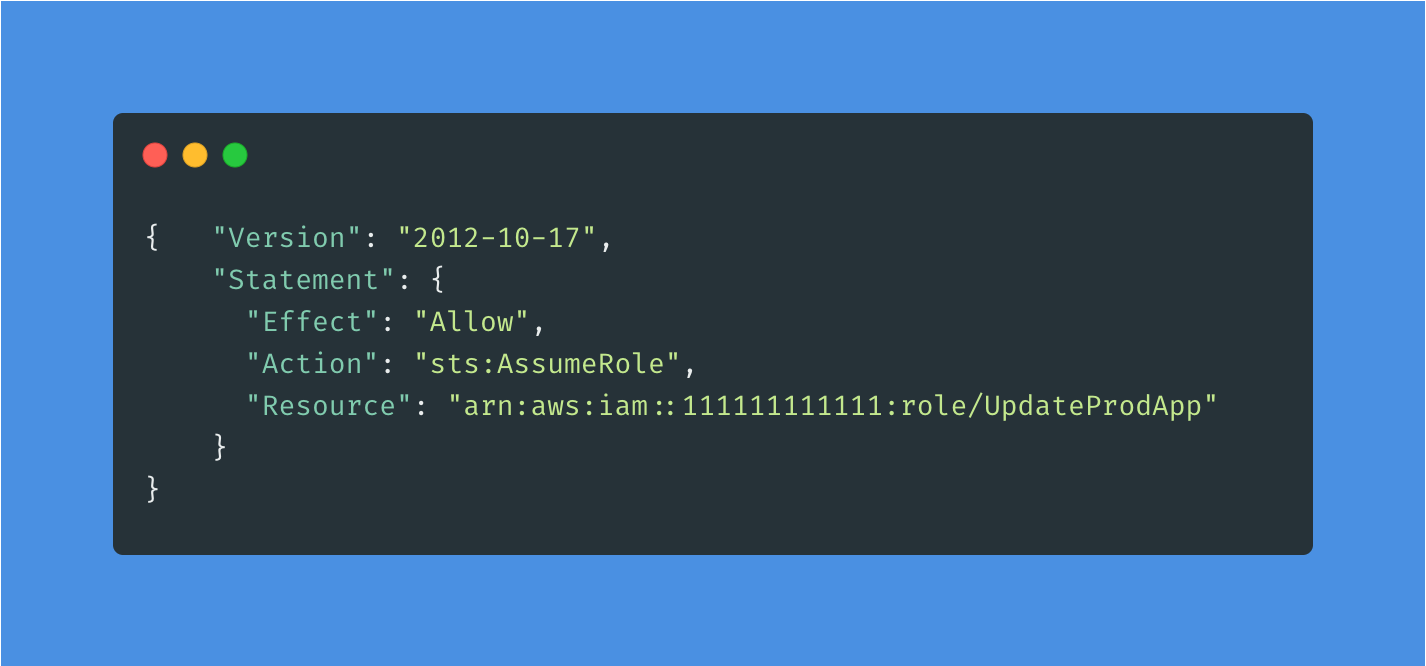
ARN is something like this. (Assume that 111111111111 is your Production AWS account Id)
arn:aws:iam::111111111111:role/UpdateProdAppOkay, now we are going to Development AWS account and add this policy to developers. You can add this a Groups or individual users. either way, you need to add this as Inline Policy.
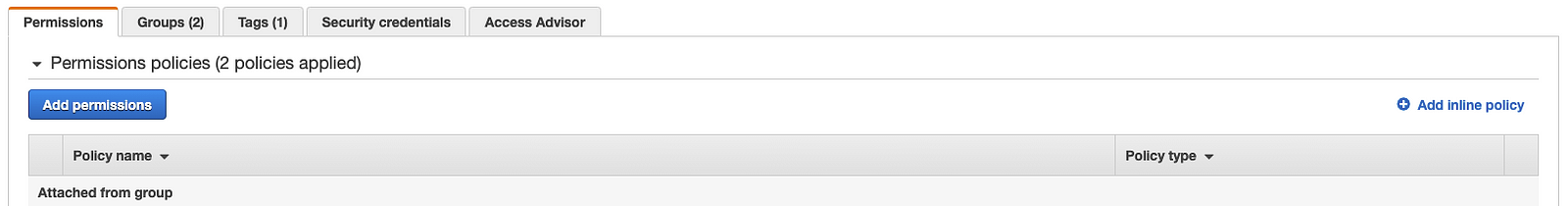
If we select a user you can find the Inline Policy from the below image. It is in the permission tab.
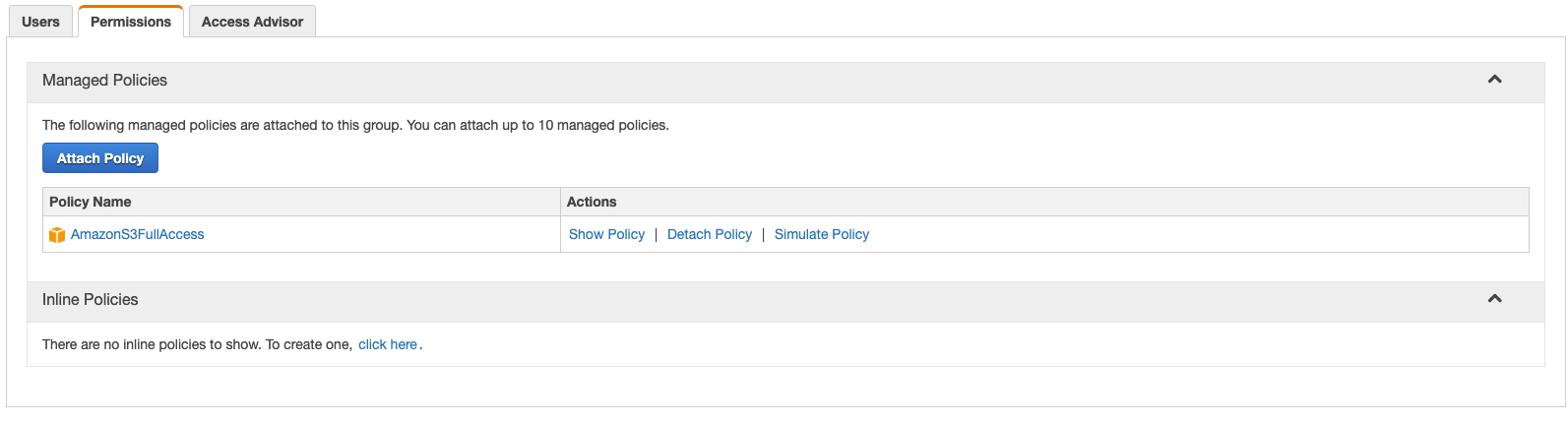
If you select a Groups you can find the Inline Policy from the below image. It is in the permission tab.
I will add this as a Group Inline Policy. Here is the policy JSON. Give a meaningful name and save it.
Now, developers can log in to Production Account. First, you need to log in to your account in Development AWS account. Then in upper right corner click on your name and it will have a dropdown list. From that list click on the switch role. At this moment you will also get an email regarding role and account details.
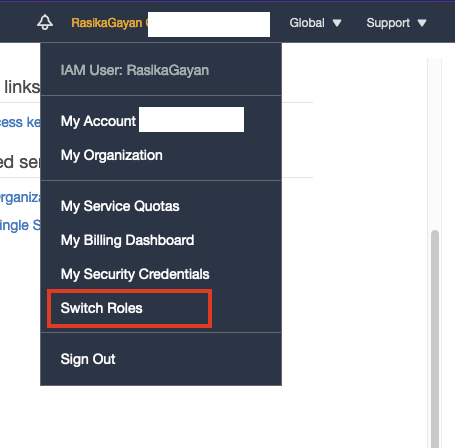
Then you will see below screen.
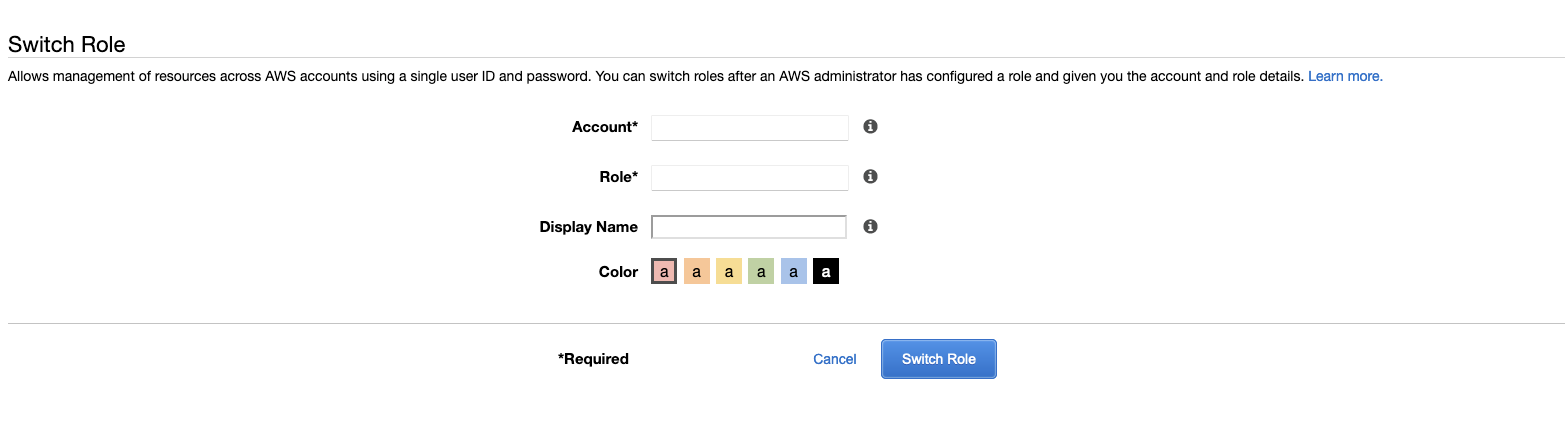
Use your role and account details and log in to it. Now you can perform relevant actions under your permission limit.
Reference:
IAM Tutorial: Delegate access across AWS accounts using IAM roles
If you have anything to ask regarding this please leave a comment here. Also, I wrote this according to my understanding. So if any point is wrong, don’t hesitate to correct me. I really appreciate you.
That’s for today friends. See you soon. Thank you
Main image credit
